Recently, the international and multi-year investigation into the criminal proxy-for-hire service named RSOCKS culminated in the seizure of the domain and dismantling of the botnet. According to the US DOJ press release, FBI Special Agent Stacey Moy said, “This operation disrupted a highly sophisticated Russia based cybercrime organization that conducted cyber intrusions in the United States and abroad.” Operators of the criminal proxy-for-hire service offered cybercriminals access to a network of hundreds of thousands of infected and compromised systems owned by individuals, businesses, and universities. Once criminals purchased access from RSOCKS, they could use the botnet to route their traffic for illicit purposes such as credential stuffing, anonymization to access hacked social media accounts, and phishing attacks.
While the June 16th DOJ press release mentioned the affidavit for the search warrant, as of the writing of this article, an indictment was not available. Thus, we do not know for certain which individuals could be charged for their involvement.
However, in a recent post on Krebsonsecurity.com, Brian Krebs’ investigation using Constella’s Hunter platform reveals evidence and insight into at least one possible RSOCKS Operator.
From his research, Krebs identifies several monikers and forums where the potential RSOCKS Operator advertised services and discussed their experience or skills. Krebs also lists a few associated domains.
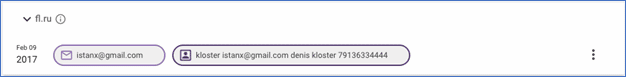
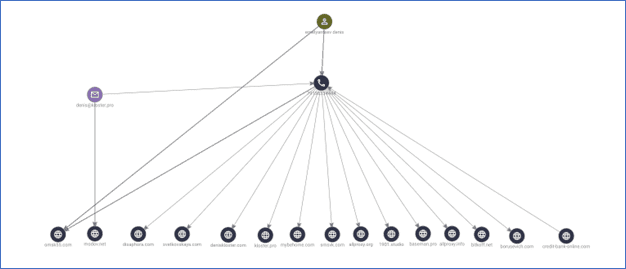
Following Krebs as he pivots through the leaked posts from darknet forum Verified, we learn the user RSOCKS previously went by the moniker Stanx; touting their expertise and advertising services related to Spamdot and RUSdot. This, in turn, is associated with the email address stanx@rusdot.com and someone named Denis “Neo” Kloster from Omsk, Russia. A related search of Denis Kloster in Constella Intelligence’s data lake of curated breached identities reveals details from the fl[dot]ru breach, including the email address istanx[at]gmail[dot]com and phone number 79136334444, a 35-year-old Russian man living abroad who also ran the world’s top spam forum.

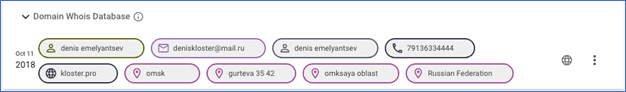
A search of the Whois database shows the domain Kloster.pro was registered by Denis Emelyantsev from Omsk, Russia, with the email address deniskloster@mail.ru and phone 79136334444.
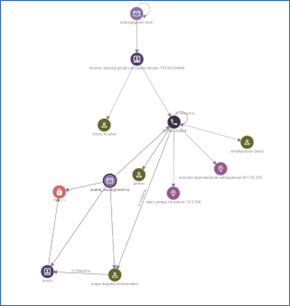
Likewise, as we continue to pivot and mine domain registrations, we can build out the following associations for Denis Kloster in Omsk, Russia; the phone number identified earlier, multiple email addresses, and domains.
Although this approach does not yield a smoking gun or any absolute correlation between a suspect and illicit activity, applying a Pivot, Farm, Mine approach to iterative investigations using various sources of commercial intelligence alongside OSINT produces strong connections for further investigation.
The full story can be found on the industry-leading blog Krebs on Security, where investigative reporter, Brian Krebs, covers online crime investigations along with the latest threats, security updates, and data breaches.
Constella Hunter
The Hunter platform is designed to improve the fraud investigation process to make it easier and quicker to unmask attackers by helping users efficiently attribute identities and identify further intelligence across multiple data sources simultaneously to expose the true identity of threat actors.