The Expanding Threat of Financial Hacks: Beyond Financial Accounts
While many associate financial hacks with stolen funds, recent incidents reveal a more complex landscape. Cybercriminals are increasingly targeting confidential employee information, which can lead to tailored phishing attacks, extortion, reputational harm, and internal disruptions within financial institutions. This blog continues our previous exploration of cybersecurity challenges in the banking and financial sector, focusing on recent breaches highlighting evolving threats to employees and customers.
The exposure of employee data—such as organizational roles, personal contact details, and work-related credentials—has become a lucrative asset for threat actors. This information enables attackers to craft convincing phishing campaigns, impersonate executives, and infiltrate critical systems. Beyond immediate financial risks, these breaches subject employees to extortion attempts, psychological distress, and potential damage to their professional reputations. Such scenarios not only harm individuals but also undermine trust in the organization as a whole.
For customers, the risks extend far beyond compromised accounts. Even when financial details remain secure, leaked personal information such as addresses, phone numbers, or account identifiers can enable identity theft and scams. Attackers often exploit this data to impersonate individuals, apply for loans, or facilitate broader fraud.
As these breaches grow in scale and sophistication, financial institutions face mounting pressure to safeguard not just customer accounts but the broader ecosystem of sensitive data. This analysis delves into recent breaches to shed light on these pressing issues and the proactive measures required to mitigate their impact.
Recent Financial Hacks & Breaches Analyzed by Constella Intelligence
1. VTB Bank – Customer Database Breach
A post on an underground forum claims to offer data allegedly linked to VTB Bank in Russia, including over 1.9 million unique email addresses. The exposed data includes personal identifiers critical for launching identity theft or phishing attacks. Given the breadth of data compromised, customers and employees alike are at risk of targeted fraud and scams.
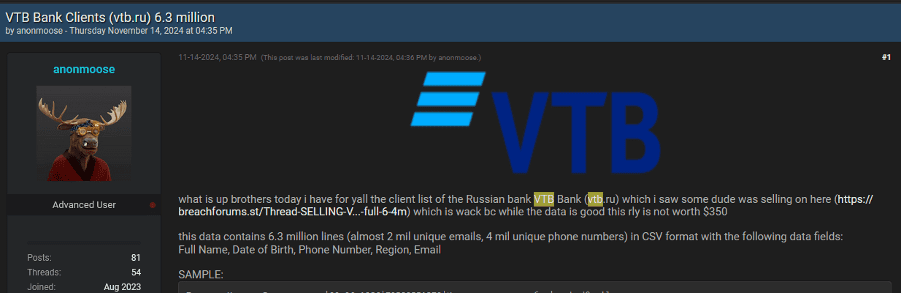
Exposed Fields:
- Names
- Emails
- Phone numbers
- Physical addresses
- Dates of birth
2. Izipay – Customer Data Breach
Izipay, a major payment processor in Peru, appears to have been impacted by a breach exposing 1.8 million unique email addresses. The compromised information encompasses extensive details about merchants, making this breach highly impactful. The data exposed is ripe for targeted attacks, including fraud schemes, impersonation, and extortion.

Exposed Fields:
- Customer codes
- Account information
- Company names
- Operational details
- Email addresses
- Phone numbers
- Regional identifiers
- Transaction data
- Administrative records
3. Interbank – Customer Database Breach
A user on a dark web platform has shared a post alleging that Peru’s Interbank was affected by a breach exposing over 1.7 million unique email addresses. The compromised information includes sensitive personal and account-related data, which attackers could exploit to defraud customers or execute targeted phishing campaigns.

Exposed Fields:
- Full names
- Account IDs / National IDs
- Birth dates
- Addresses
- Phone numbers
- Email addresses
- IP addresses
- Credit card information
4. Bank of America – Employee Directory Breach
In the United States, Bank of America reportedly experienced a breach tied to the MOVEit vulnerability, compromising more than 280k unique emails. The breach exposed extensive employee directory information, making it a prime target for attackers seeking to craft social engineering schemes. The detailed organizational data presents significant risks, including impersonation of high-ranking officials and exploitation of internal processes for financial gain.
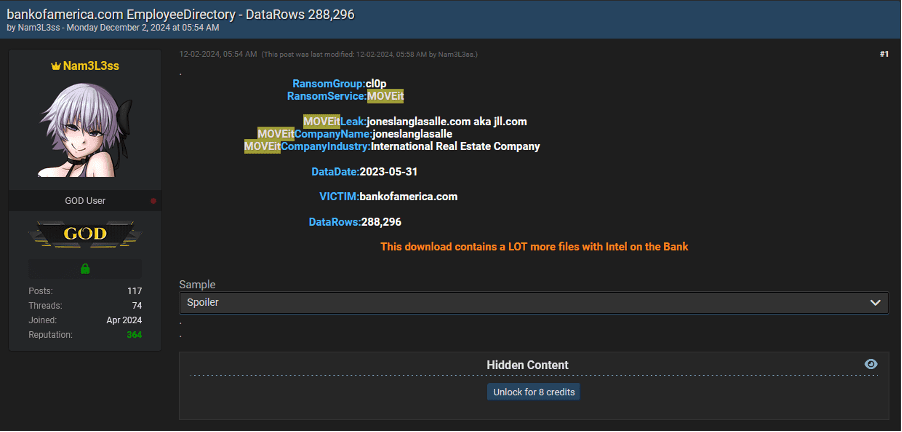
Exposed Fields:
- Employee codes
- Login IDs
- Full names
- Email addresses
- Phone numbers
- Job titles
- Detailed organizational information
5. PrivatBank – Customer Data Leak
Data sets allegedly tied to Ukraine’s PrivatBank, including over 400 unique emails and 237 million records, are being offered for sale online. While the number of email addresses found was low, the leak’s volume and the type of data—personal identifiers like passports and full names—pose a severe risk. Cybercriminals can use this information for identity theft, document forgery, or large-scale fraudulent activities.
Exposed Fields:
- Login IDs & Emails
- Full names
- Phone numbers
- Passport information
Conclusion
These breaches illustrate the growing sophistication of cyber threats targeting financial institutions. While direct financial theft remains a concern, the exposure of employee and customer data introduces new risks, including identity theft, extortion, and reputational damage. Addressing these challenges requires proactive and comprehensive cybersecurity measures.

