Bank breaches and the banking world are now a front line in cybersecurity, where hidden networks thrive in the shadows of the dark web and encrypted chats. As technology advances, the dangers of bank hacks grow, transforming old-school bank robbers into modern cyber thieves who operate from behind screens worldwide.
Social media, especially platforms like TikTok, Instagram, and Twitter, play pivotal roles in this shift. Hashtags like #CCCard, #CardCloning, and #CloningCards aren’t just trendy—they’re where cybercriminals mingle, share hacking tips, and flaunt their crimes.
These platforms, along with encrypted apps like Telegram and dark web marketplaces, form a kind of cybercriminal university. Here, new hackers can learn everything from cloning cards to cracking bank security, all shared openly in tutorials and forums. This easy access to criminal resources marks a stark evolution from the masked, gun-toting bank robbers of the past to today’s sophisticated digital thieves.
Below, you’ll find screenshots that capture these exchanges, highlighting how these digital platforms have reinvented the concept of bank robbery, giving it a vast, tech-savvy reach.
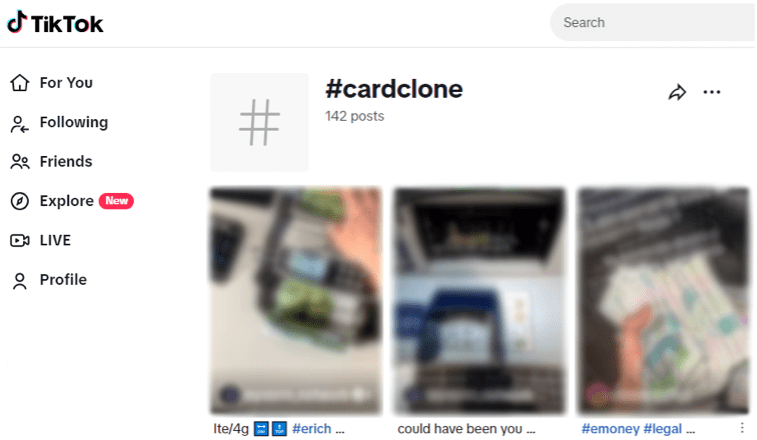



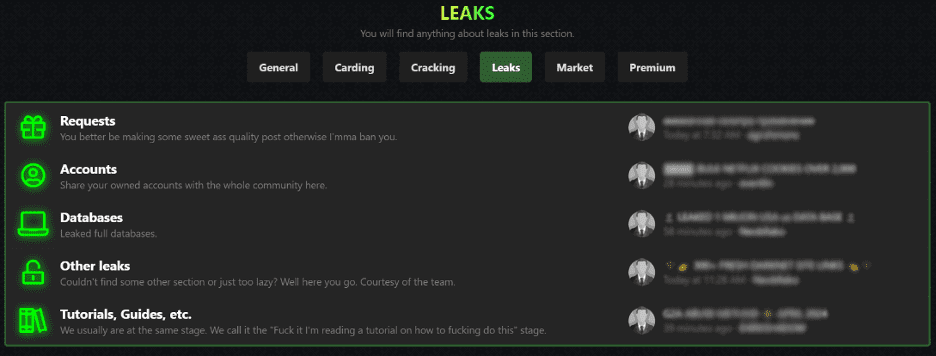

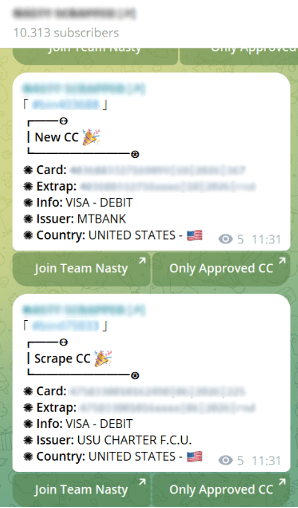
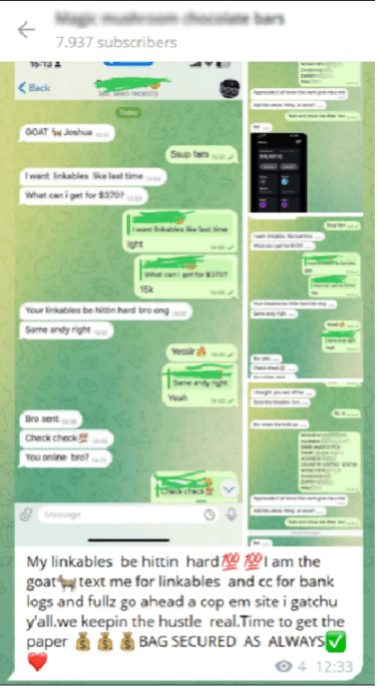
Navigating the digital frontier, it’s evident that traditional security measures no longer suffice against the advanced tactics of today’s cybercriminals. This shifting landscape demands more robust and adaptive security strategies to protect sensitive information.
At Constella, we have compiled a concise summary that reflects our ongoing focus on the latest data breaches we’ve uncovered on the Dark Web. Below, we detail these findings.
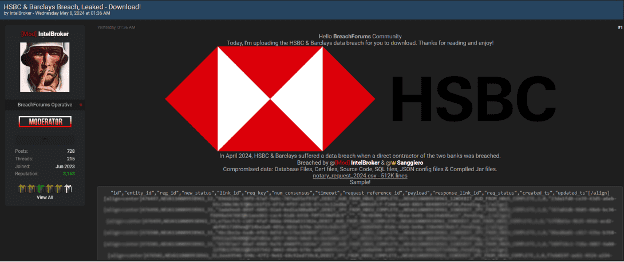
Bank Breach – HSBC & Barclays
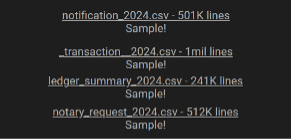
Last May 8, one of the moderators of this breaches forum, called “IntelBroker” (very renowned actor), and another member named “Sanggiero”, published several CSV files, concretely, if we add up all the records of all the documents, there would be more than 2 million records, with valuable information of users of two of the most internationally known banks, these files specifically contain:
- Database Files.
- Certificated files.
- Source Code.
- SQL files.
- JSON config files.
- Compiled Jar files.
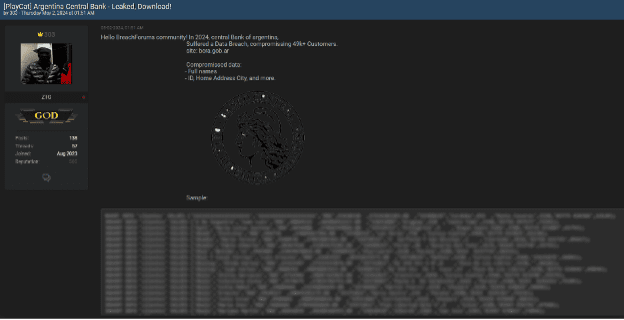
Bank Breach – Argentina Central Bank
On May 2nd, a significant banking breach was reported by a user known as ‘303’, who has a solid reputation on the forum. Although the exact date the breach occurred wasn’t specified, the user noted that the data is from 2024. This breach impacted over 49,000 customers, exposing sensitive information including:
- Customers’ full names
- ID numbers
- Home addresses
- Cities
Bank Breach – Kernel Finance
On April 26th, a threat actor named ‘netnsher’ potentially targeted ‘India’s Simplest GST Billing Solution’, Kernel Finance, leading to a data breach that exposed over 7,000 bank account numbers and sensitive information. Within this breach, the following type of information can be found:
- Id.
- Created_at.
- Updated_at.
- Deleted_at.
- Created_for_account.
- Document_type.
- Reminder_period_type.
- Reminder_receiver_type.
- Trigger_period_days.
- Is_enabled.
- Resource_type.
- Additional_fields.
- Created_by_user.

Bank Breach – M&T Bank
The same day, April 26th, this threat actor, “netnsher”, exposed data over 600 rows of access tokens and essential files of the Law Firm Banking Trustnota by M&T bank. All this information could be current active access tokens, as the threat actor said that any user with access to the accounts can get a lot of money. The information includes:
- Bank account details
- Residential locations
- Other personal data (National ID, Age, Status, etc…)

The breaches we’ve discussed here are just a few examples of what’s been happening on the Dark Web over the last few weeks. These incidents highlight the ongoing and very real threats that exist online, especially in hidden corners of the internet. To help protect yourself, here are some straightforward tips:
- Be Cautious with Personal Information: It’s crucial not to share sensitive details like your social security number or bank account information with people you don’t know. This can help prevent identity theft and fraud.
- Use Virtual Cards for Online Purchases: If possible, opt for virtual credit or debit cards when shopping online. These provide an extra layer of security by masking your real card details and keeping your primary accounts safer.
- Subscribe to an Identity Monitoring Service: Consider using a service that monitors your identity. These services can alert you if your personal information is being used without your permission, helping you respond quickly to potential threats.
Taking these steps can enhance your defenses against the types of cyber threats that are becoming more common in our increasingly digital world.