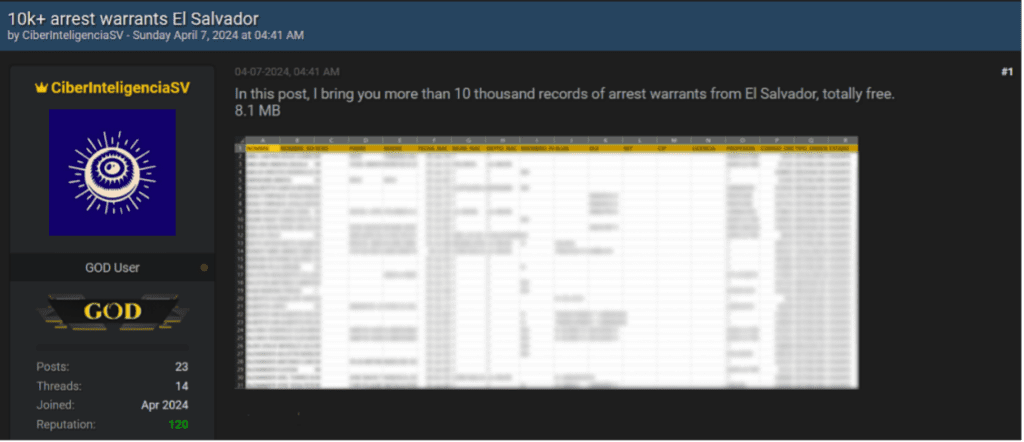
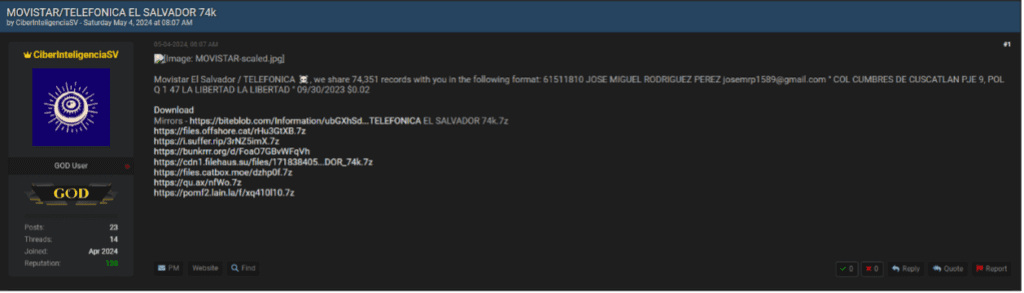
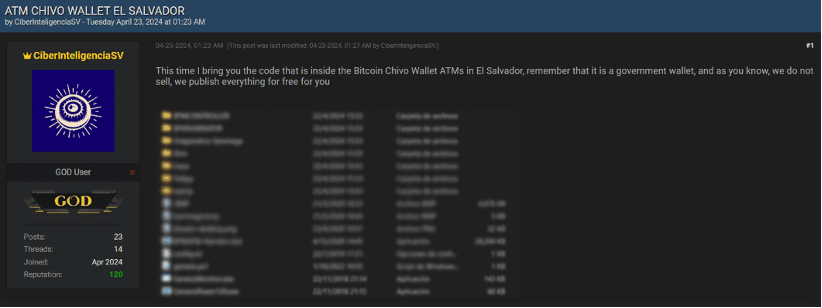
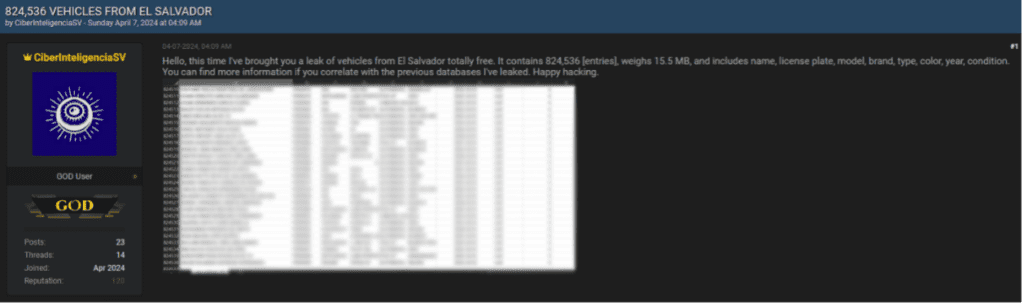
Leveraging Infostealers to Breach Companies: A Cybersecurity Intelligence Perspective
Infostealers are specialized malware designed to extract sensitive data from infected systems. They operate in the background, collecting login credentials, browser histories, and cookies, often without detection. Deployed through phishing emails or malicious websites, infostealers are a growing favorite among cybercriminals due to their low risk of detection and the high-value data they yield.
Unlike more overt forms of cyberattacks like ransomware, infostealers are subtle and continuous. The stolen information is often sold in bulk on dark web marketplaces or used to launch further attacks, such as gaining access to company networks or committing financial fraud. The sophistication of these tools has grown, making them one of the most effective methods for threat actors to compromise corporate environments.
Why Infostealers Are Effective Against Companies
Infostealers are attractive to threat actors for several reasons:
- Low Detection Rates: Infostealers are designed to evade detection by traditional security measures such as antivirus software. Once deployed, they blend seamlessly into legitimate system processes, making it challenging for conventional security solutions to recognize or remove them. This stealth allows them to operate undetected for extended periods, gathering critical data.
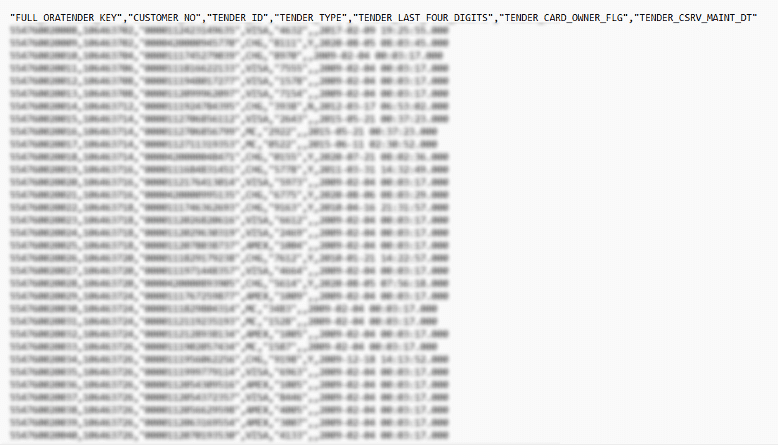
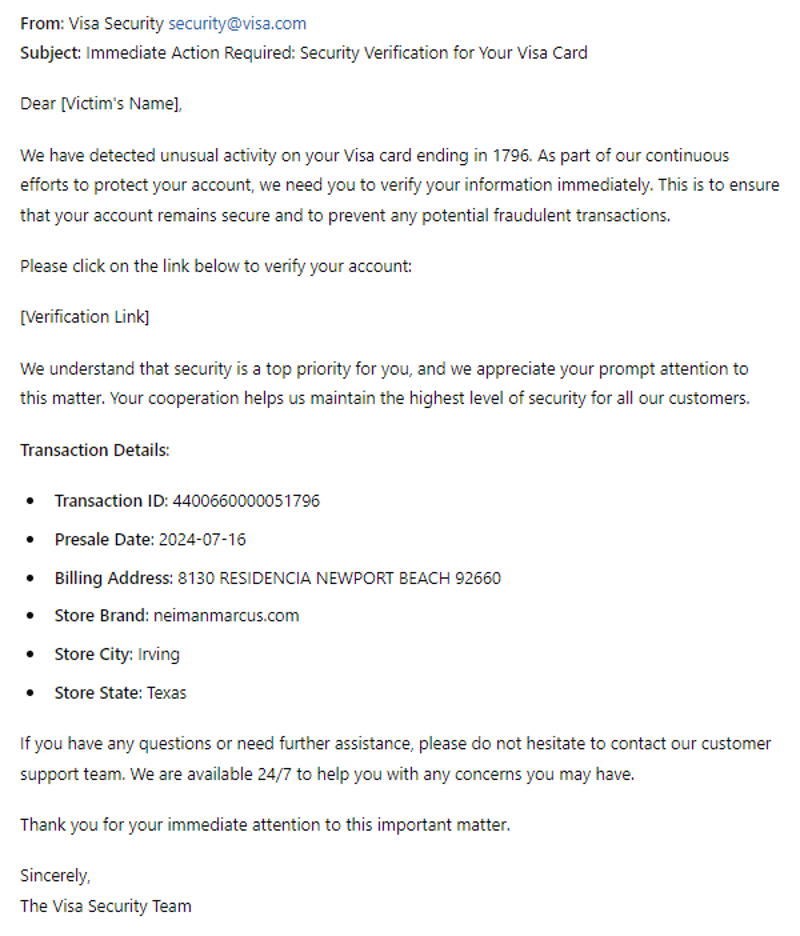
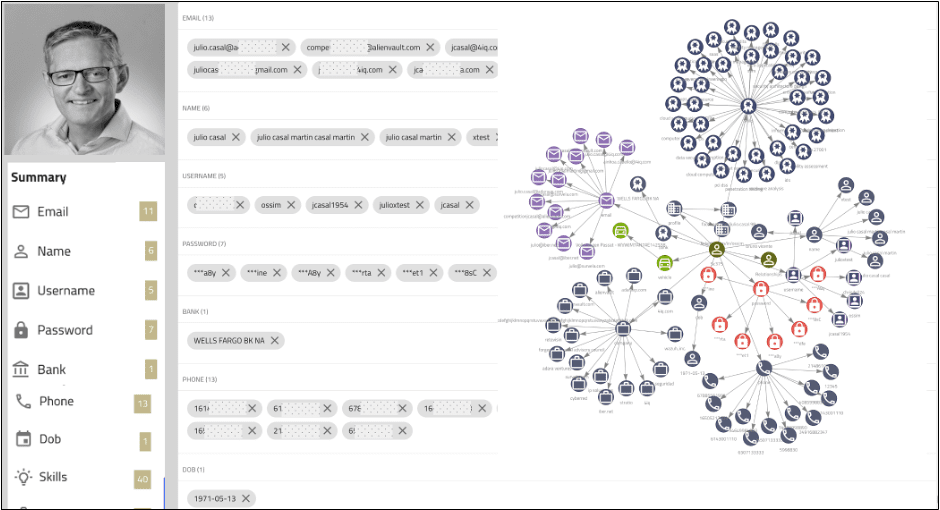
- Targeting High-Value Data: Infostealers are capable of extracting a wide range of sensitive information, including passwords, session cookies (which can be used to bypass multi-factor authentication), financial records, and proprietary business data. This stolen data is often sold on dark web marketplaces or used for extortion, leading to significant financial and reputational damage.
- Wide Availability and Accessibility: Infostealers are readily available for purchase on dark web forums, frequently offered as part of malware-as-a-service (MaaS) platforms. This makes them accessible even to less experienced cybercriminals, lowering the barrier to entry for launching sophisticated attacks. The ease of access and customization further amplifies their appeal to threat actors across the cybercriminal ecosystem.
Top Threat Actors Leveraging Infostealers
We have seen that many cybercriminals are actively using infostealers data as a preferred method for infiltrating organizations. These groups have leveraged infostealers to breach companies, leading to extensive financial and reputational damage. Below are a number of threat actors that stand out for their sophisticated use of these tools:
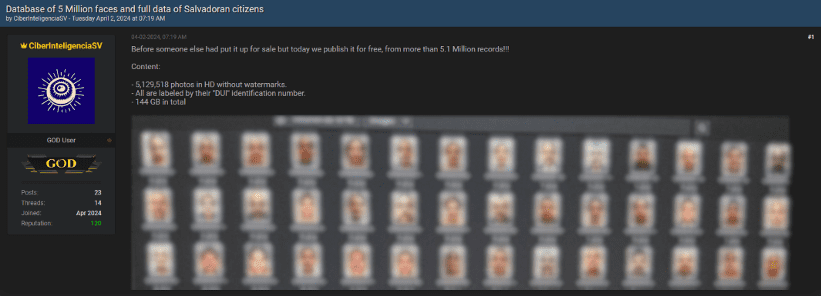
- USDoD: This threat actor has carried out high-profile attacks, including the breach of Airbus by exploiting compromised credentials from a Turkish Airlines employee. This attack underscores the significant risk that infostealers pose to supply chains, allowing hackers to penetrate companies through vulnerable third-party partners.
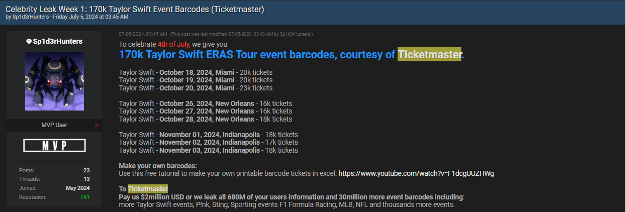
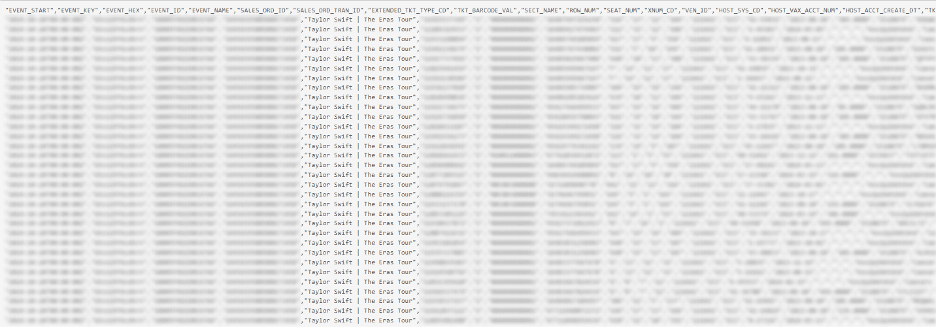
- Sp1d3rHunters: Known for exploiting Snowflake accounts, Sp1d3rHunters has executed breaches against major companies such as Ticketmaster and AT&T, exfiltrating sensitive data such as customer information and event tickets. Their operations demonstrate how infostealer logs can be used to gain access to cloud services and wreak havoc.
- IntelBroker: This notorious threat actor has breached both government and private sector entities, targeting organizations such as Apple, Zscaler, and Microsoft. By using Infostealer-collected credentials, IntelBroker has facilitated attacks on critical infrastructure and sold access to compromised systems on dark web forums, further intensifying the risk to companies.
- Andariel (North Korea): Part of the Lazarus Group, Andariel is a North Korean state-sponsored Advanced Persistent Threat (APT) actor. This group is known for using infostealers, alongside other tools like keyloggers and remote access trojans (RATs), to target sectors such as military, nuclear, and manufacturing. Andariel’s strategy of using Infostealers to gather intelligence and financial data is a key part of their cyber operations.
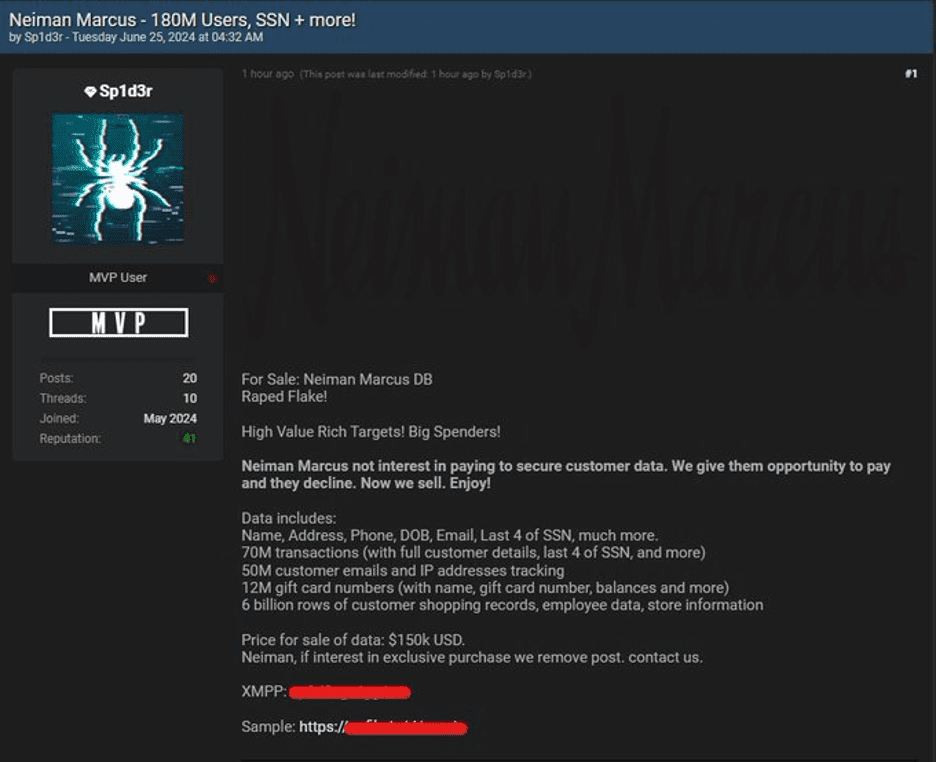
- Lapsus$: Emerging in 2021, Lapsus$ has quickly gained a reputation for its high-profile breaches of companies like NVIDIA, Samsung, and Vodafone. Lapsus$ utilizes info stealers to harvest login credentials, payment information, and proprietary business data. In a notable attack, Lapsus$ breached Electronic Arts (EA), stealing source code for popular games like FIFA. The group’s aggressive tactics have caused widespread disruption in the tech and financial sectors.
These groups’ sophisticated use of infostealers illustrates why businesses must adopt more advanced detection and monitoring systems to protect against this growing threat.
How Companies Can Defend Against Infostealers
While info stealers present a complex threat, companies can adopt several key strategies to mitigate the risks and minimize the impact of such attacks:
- Analyze Exposed Data for Risk Mitigation: After a suspected infostealer attack, companies must conduct thorough analyses of the stolen data to assess the potential risks. This includes examining session cookies that could be hijacked to bypass multi-factor authentication (MFA), as well as personal credentials that may be used to impersonate employees or escalate privileges within the organization. Proactively identifying and addressing these risks can help prevent follow-up attacks or unauthorized access.
- Strengthen Authentication Practices: While MFA is an essential safeguard, it is not foolproof, especially if session cookies are compromised. Companies should implement adaptive MFA, which monitors for anomalies in login attempts (such as unusual locations or devices) to prevent attackers from using stolen credentials. Additionally, frequent reauthentication can help disrupt the use of stolen session tokens.
- Monitor for Unusual Access Patterns: Regularly reviewing access logs and monitoring for anomalous login attempts—such as multiple failed attempts, logins from unexpected locations, or odd behavior patterns—can help detect infostealer activity early. Endpoint Detection and Response (EDR) systems can play a key role in identifying and mitigating the effects of infostealers by flagging unusual data access or exfiltration activities.
- Educate Employees on Phishing and Cyber Hygiene: Many infostealers are deployed through phishing attacks or malicious links. Regularly training employees to recognize suspicious emails, websites, and attachments can significantly reduce the likelihood of an initial infection. Implementing phishing simulations and real-time feedback can help maintain employee vigilance.