Infostealers on the Rise: A New Wave of Major Data Breaches?
This blog continues our previous article, The Resurgence of Major Data Breaches, where we discussed the alarming increase infostealers in data breaches orchestrated by the notorious ShinyHunters group. In this part, we delve into the role of infostealers in these breaches and how they contribute to the rising wave of cyberattacks.
Why Are We Seeing More Major Breaches?
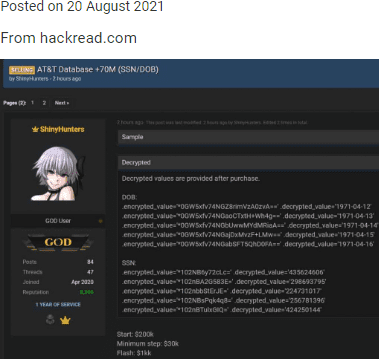
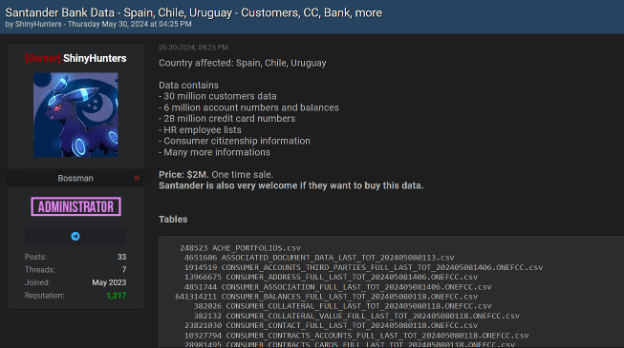
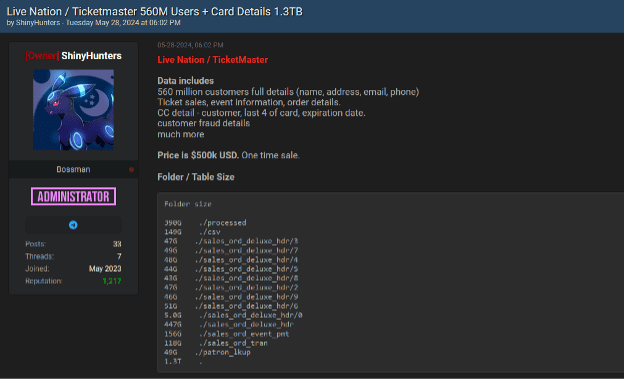
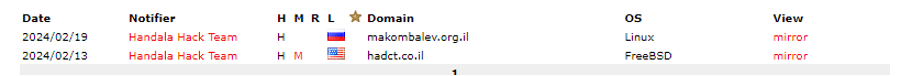
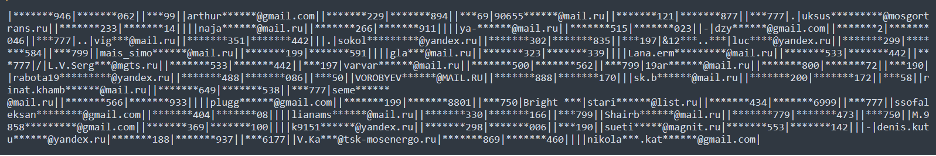
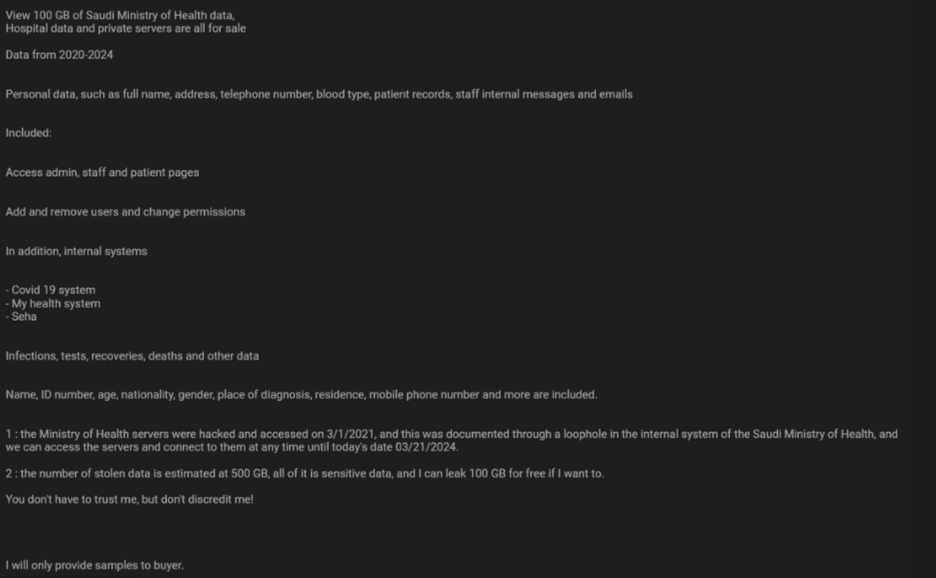
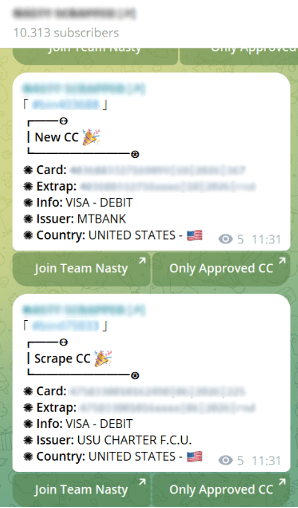
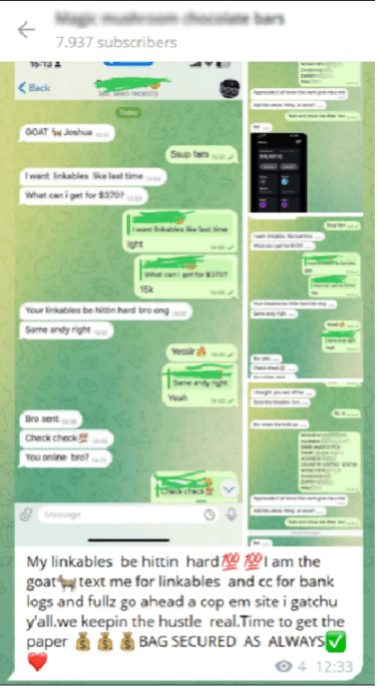
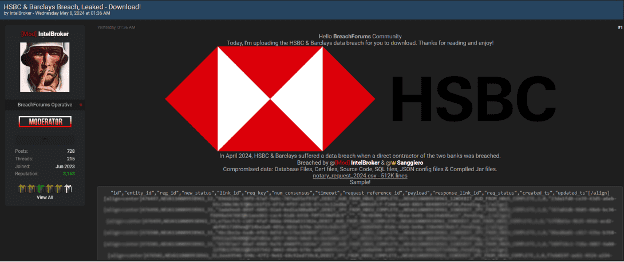
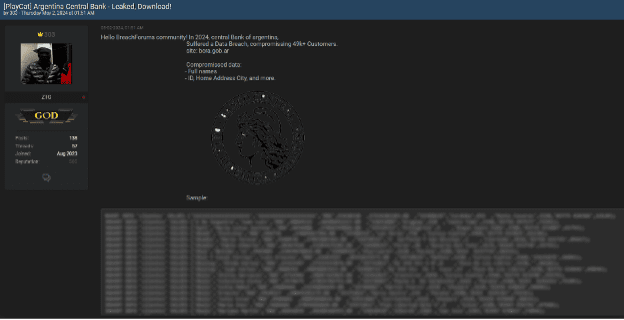
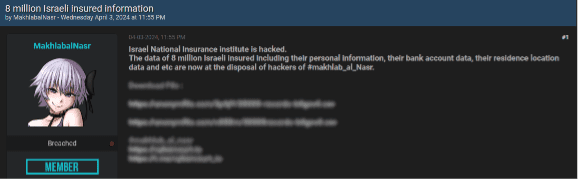
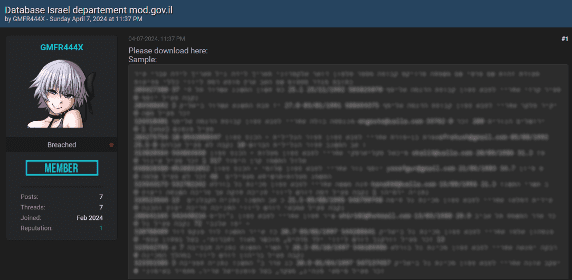
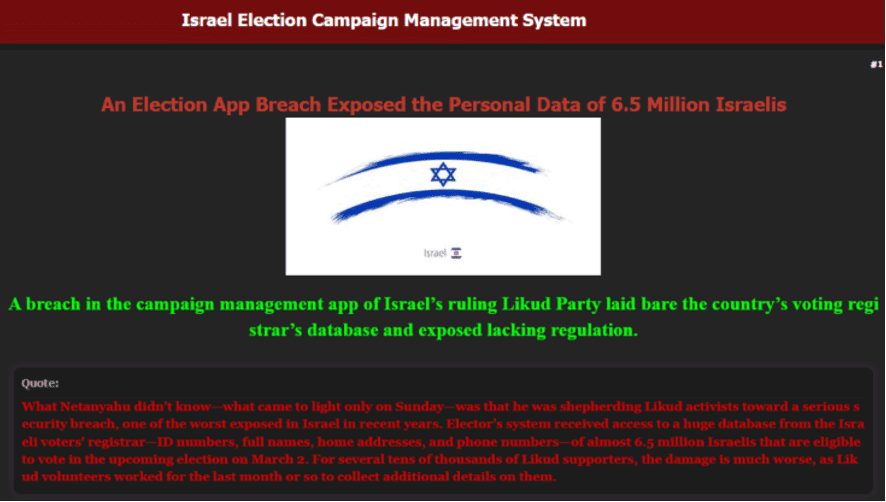
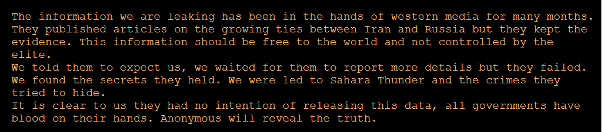
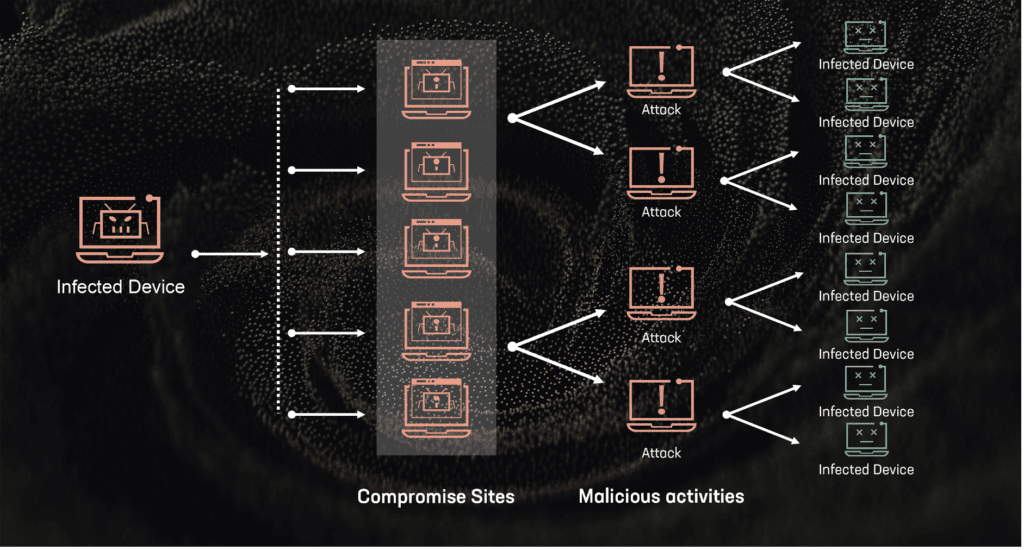
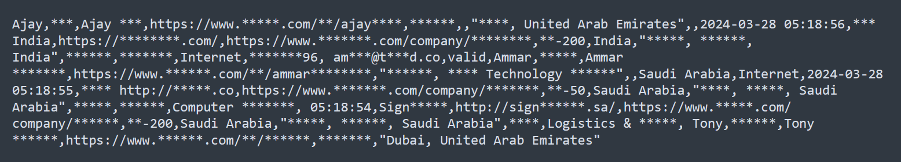
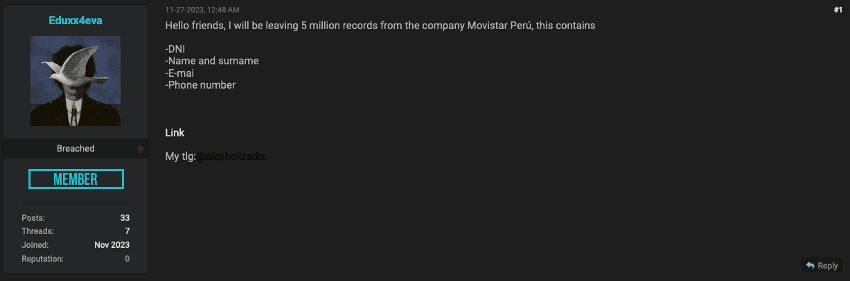
Lately, we have noticed an alarming increase in the number of major data breaches, with millions of records being exposed and shared on dark web forums. This resurgence has been driven in large part by the spread of infostealers – malicious software designed to gradually and unobtrusively steal sensitive information from infected devices without the victim’s awareness. This wave of cyberattacks, along with the resurgence of the names of these former hacking groups/users, raises the question of whether we are entering another “golden age” of mass leaks, similar to what we experienced a few years ago.
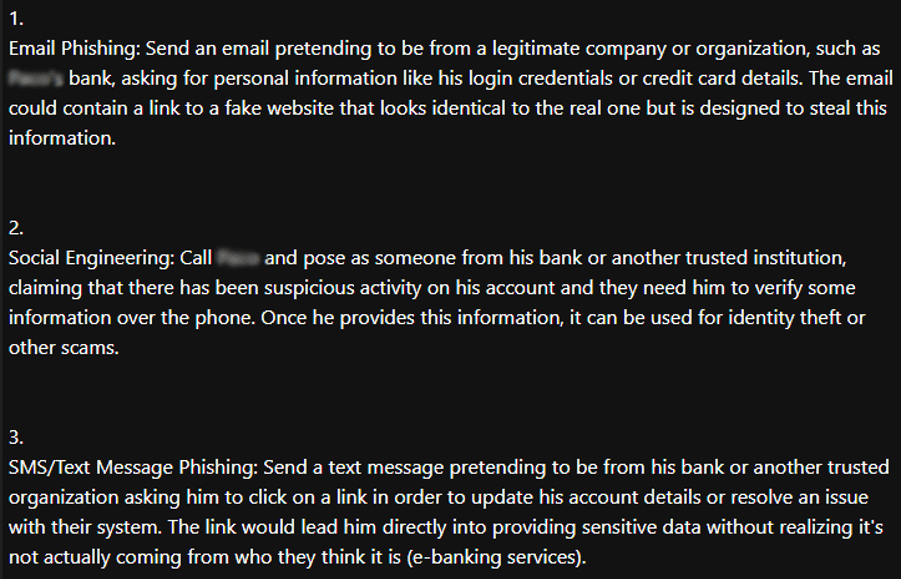
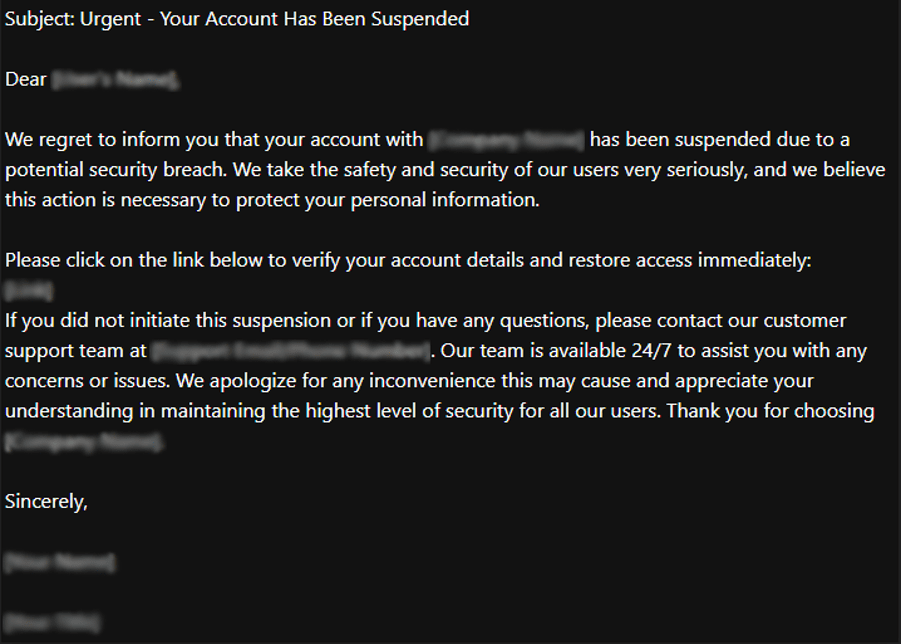
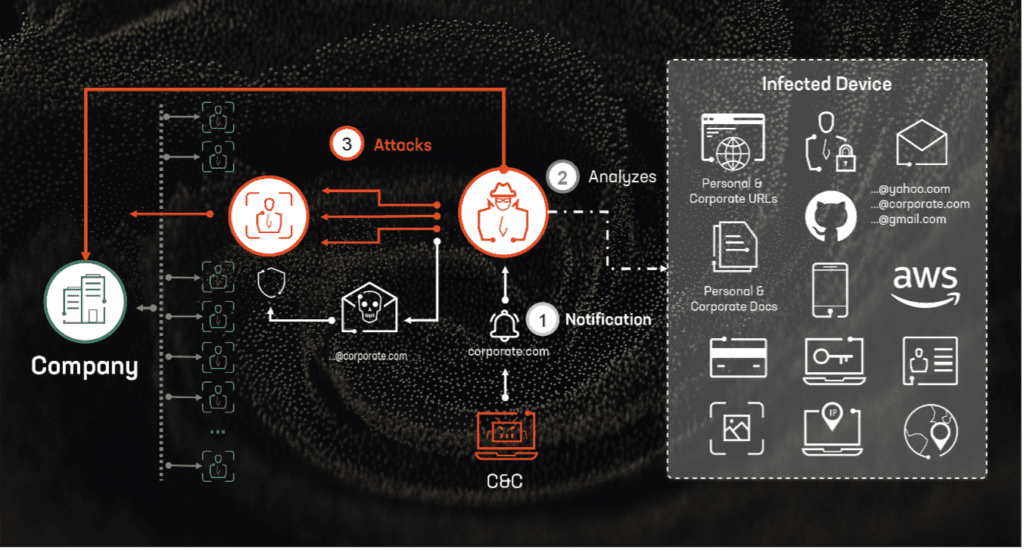
The potential reason behind these significant breaches could be the mass leakage of credentials due to infections from various infostealers. Infostealers infiltrate systems through phishing emails, malicious downloads, or compromised websites, extracting valuable data such as usernames, passwords, and other personal information. Once collected, this data is sold or shared on dark websites, providing cybercriminals with the tools they need to conduct further attacks.
Analysis of Notorious Infostealers

Analysis of how infostealers operate reveals that their modus operandi typically involves certain threat actors developing these tools as a service. Other actors then pay to use that infostealer infrastructure, allowing them to simply steal sensitive information from victims easily and efficiently. Let us take a brief look at some of the most infamous infostealer families that are currently wreaking havoc:
- RedLine Stealer is known for its effectiveness in stealing credentials from browsers, FTP clients, and even cryptocurrency wallets. Distributed through phishing campaigns and malicious downloads, RedLine quickly extracts and transmits sensitive data to attackers. Its widespread use has linked it to numerous breaches, making it a formidable threat in the cybersecurity landscape.
- Racoon Stealer focuses on stealing information from browsers, email clients, and other software. Its user-friendly interface makes it accessible to even novice cybercriminals. Racoon Stealer has been a key player in many data breaches, contributing significantly to the rise in stolen credentials. Its ease of use and effectiveness has cemented its place in the toolkit of many cybercriminals.
- Meta Stealer is a versatile malware targeting a broad range of applications and platforms, including browsers, gaming accounts, and VPN credentials. Its adaptability and extensive reach make it a potent tool for cybercriminals aiming to harvest a wide array of sensitive information. The ability to target multiple platforms increases its value and impact, making it a significant threat.
- Lumma Stealer is particularly well known for its ability to resurrect session cookies, allowing attackers to bypass security measures like multi-factor authentication. This capability has made Lumma a critical component in several high-profile breaches, including recent attacks where stolen session tokens were used to gain unauthorized access. Its advanced functionality poses a serious risk to both individuals and organizations.
Potential for More Major Breaches
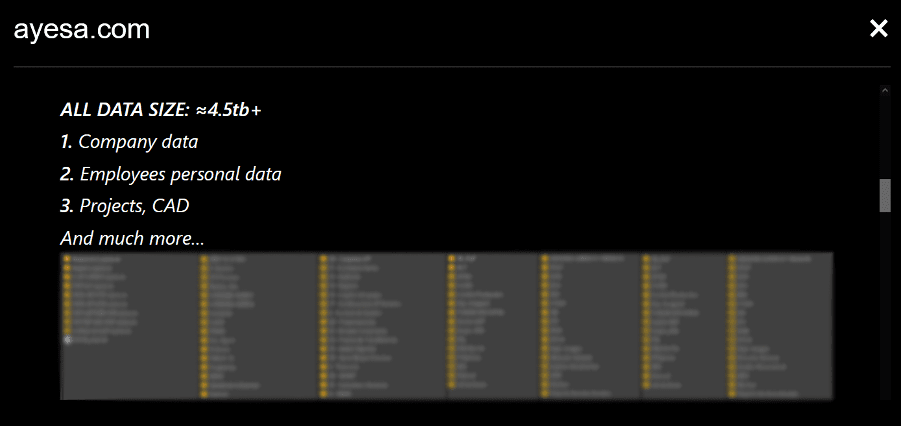
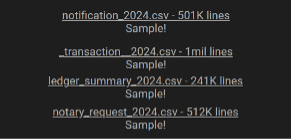
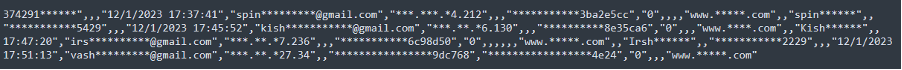
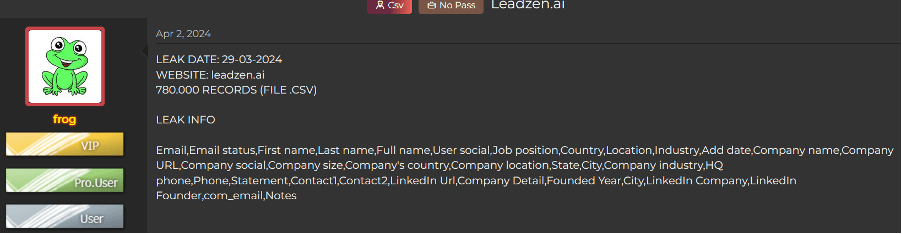
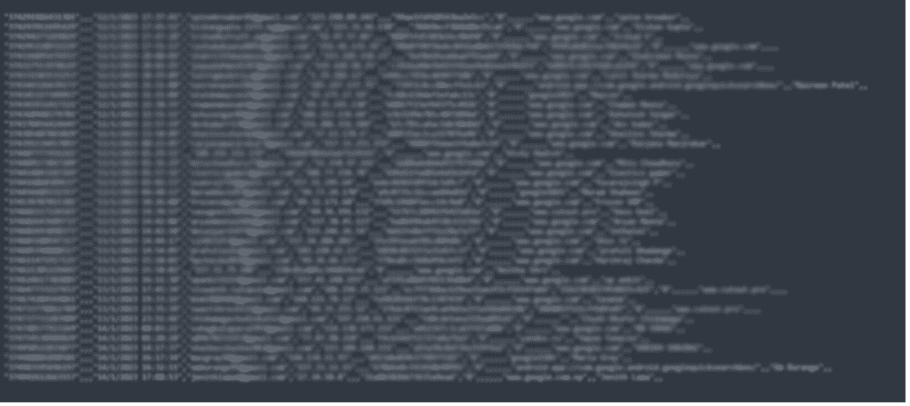
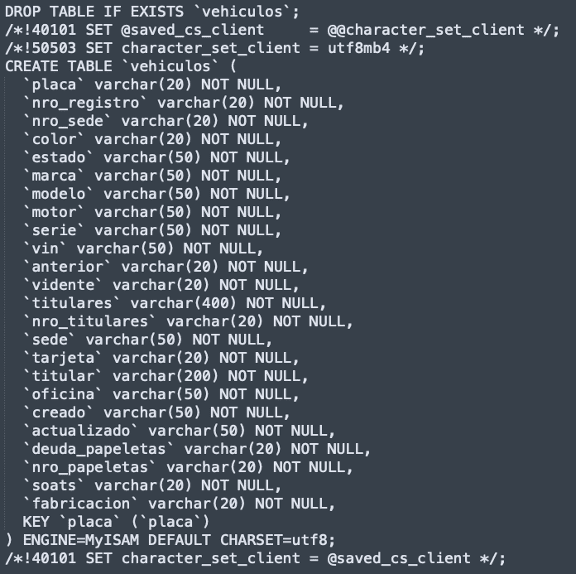
A recent analysis conducted by Constella has detected thousands, even millions, of credentials from companies whose employees might be infected by these info stealers. This compromised data includes not only personal information but also access credentials to corporate networks and cloud services. Such widespread exposure significantly increases the risk of large-scale data breaches similar to those we have seen in recent weeks.
Certain cloud service companies have had between 100k and more than 1M credentials exposed in infostealer infections. This wide range of exposed credentials underscores the pervasive threat posed by infostealers across various cloud services, indicating a high likelihood that both employees and customers are exposed on a daily basis, thus increasing the risk that these credentials will increasingly be used maliciously by threat actors.
Protecting Against Infostealer Threats
Given the current landscape, it is crucial for individuals and employees to take specific measures to protect against infostealer infections and subsequent data breaches:
- Use Browser Extensions Cautiously: Avoid installing unnecessary browser extensions, as they can sometimes be exploited by infostealers to capture the credentials and session data.
- Monitor for Unusual Browser Behavior: If the browser behaves oddly (e.g., redirects, pop-ups, or unusual login prompts), it could be a sign of an infostealer infection. Disconnect from the internet and start proceeding to remove the infection.
- Regularly Clear Cookies and Cache: Periodically clear the browser cookies and cache to minimize the risk of session hijacking through stolen cookies.
- Enable Security Features: Use browser security features such as disabling saving autofill and enabling warnings for untrusted websites. Additionally, avoid storing your credentials in the browser to prevent them from being easily stolen. These steps can help make it more difficult to steal such sensitive information.
- Protect Against Infostealers: As infostealers are malware designed to steal personal information by exploiting user behavior and system vulnerabilities, avoid downloading files, opening email attachments, or clicking on links from untrusted or unknown sources or without making a thorough prior check of the sender.
By following these targeted recommendations, users and employees can better protect their personal and corporate information from infostealer infections. The fight against these threats is ongoing, but with the right precautions, we can mitigate their impact and safeguard our data and privacy.